Karibuni wakufunzi wote!

"nakukabidhi mwenge"
Welcome TTC Tutors to the new Blog for ICT Departments at Teachers Colleges’ around Tanzania. I am a USA Peace Corps volunteer who has been working at Mpwapwa TTC since 2007. Over the next two months I would like to share many things we use at Mpwapwa TTC to make our lives easier at our ICT department. I always enjoy visiting wakufunzi wa taifa to share these tips. I have already visited 6 of the 33 colleges from Butimba to Vikindu, but I think it is difficult to visit more. I want to be free to focus on new projects in Mpwapwa before I finish my contract at the end of the year. Instead of visiting you, I’ll be offering the tips here. For the first month, every three days I will post a new entry, some of the topics I will be talking about are in the list below.
I will assume that your college is working with the Solaris system the Wakute Project put together in December 2008 with a new user management website (if that link doesn’t give an error, you are ready!). I’m also pretty sure that you have many Windows XP computers around your ICT center so I will have tips for those too. More resources are available at the Wakufunzi Google Group but these will be openly available for easy access and better organization.
I will try to include good instructions so that you can use the tips to improve your work at your TTCs. If you ever have questions I’m always happy to answer via email or text. I am on Zain at 0782516598, yahoo IM at thadk, and skype at thadknull.
Some things that I already plan to cover:
- Ideas on viruses and how they’re spread in East Africa, how you can control them.
- Three ways to show the hidden files on your USB flash and why viruses hide them. Even when viruses delete the files instead of hiding them there are good programs to try to recover your files (if you haven’t used the flash again)!
- How to access free video Solaris training materials at your TTC.
- Why is the internet slow today?
- How to set up a proxy server with Ubuntu to filter
- How to enable printing and the difficulties
- What should you include in a resources folder for your students?
- My bookmarks keep getting erased! How can I have my bookmarks anywhere duniani?
- Using Windows & WinSCP to download files like a flash from Solaris: tips and tricks with screenshots
- How to add sections to word processing documents so that roman numeral page numbering (i,ii,iii) and normal numbering can be in the same document in OpenOffice and Word.
- “Cloning” a lab of Windows or Ubuntu desktops with CloneZilla so you can install Windows once and refresh dirty computers in 20 minutes to an “image” that is saved on your Solaris Server or flash drive.
- What is fiber, when is it coming to my TTC and why does it matter for TZ?
- The importance of power protection in Tanzania, problems already seen at TTCs (save your comments!) and what to buy for your computer to prevent it from dying.
Nashukuru sana, urudi tena tafadhali!
thadk
Safi Software
If you are using Windows, then I have some free software for you to try today.

NetLimiter Monitor Free is software that will watch to see how much of your internet speed is being used by each program on your computer. For example, you can see how many megabytes you downloaded with Mozilla Firefox on 21 September 2009. You can also see what is using all of your download speed or upload right now. Remember, each college’s VSAT has only 3kiloBytes per second to send data for all users to share! (between 30 and 200kiloBytes per second to recieve data: much bigger)
Paint.NET is a program that can help you to make simple diagrams and to clean photos or screenshots such as the one above. It is simple to use like Microsoft Windows Paint but much stronger. You might need the “.NET Framework” in order to use it, this is like downloading Java (or Adobe Flash for your web browser).
VLC (“VideoLan Client”) is a powerful movie player than can play any kind of movie.
Google Picasa is a good program to manage your digital photos.The version 3.5 will even find faces in your pictures so that you can quickly see all the digital pictures from one person.
WinDirStat is a good program to help you find what is taking up all of your hard disk storage space on Windows. It makes an interactive graphic of all of your files and their sizes.
Life and Death of Storage Devices 3: Mechanical Hard Disks
Mechanical hard drives have been inside computers for a very long time, perhaps since the late 1980s. Like floppy disks, they rely on magnetic technology to store data on discs but the technology had become so advanced and sensitive that they switched from plastic to metal and needed to put the discs in a very closed box.
The factories that make hard drives have no dust in them. The air processors remove it so that the magnetic particles in the dust doesn’t interfere with the magnetic particles in your drive. Before the hard drive leaves the factory they seal it making it impossible for dust to get inside but also impossible to repair.

Open Hard Disk platter
In all mechanical devices (as we saw with the failure of CD-ROM drives in part 1), there are parts that wear down from use or from a bad environment. For a hard drive the worst environment seems to be poor voltage control but temperature & handling also play roles. The motors in hard drives, especially laptop hard drives seem especially sensitive to input voltage fluctuations, or changes, from 230V.
In a hard drive there are motors which spin the discs, there are motors which move the read/write magnet arm and there are micro processors, chips which control the operations. If any of these are damaged, they are nearly impossible to fix. Umeme uchafu is probably the most common way for hard drives to die in Tanzania. A spike might kill the chips and inconsistent voltage might wear down one or both of the very accurate motors.
If a laptop drive (2.5″) is dropped while it is running, the magnetic arm will crash into the discs causing a small dent or permanent destruction. If they’re dropped when turned off they’re impressively tolerant. Desktop sized (3.5″) hard drives are even more sensitive to being dropped, even when turned off.
Voltage Regulator, useful for laptops
Hard drive deaths are mysterious. Google has millions of hard drives in its facilities and it has published papers on the strange and random ways they fail. There are very few definite patterns, especially here in Africa. Even in a perfect environment with air conditioners, perfect power and care when handling they can fail. The most important things are to be preventative by using power cleaning devices and keeping backups.
One pattern which is worth noting is that once hard drives have lived past 1yr of consistent use they’re likely to continue to last, provided good voltage, handling.
In my opinion, you should get a voltage regulator to protect from inconsistent voltage on laptops and some form of AVS for a desktop. Keep in mind a voltage regulator will not protect from very big spikes or surges such as transformer explosions. At our TTC we have seen UPSs behind voltage regulators die even after the fuse has burnt.
Life and Death of Storage Devices 2: USB Flashes / Camera memory
As I’d mentioned in the first section of this series on CD-R and DVD-R, East Africa is a rough environment for storage devices. The last 3 years have seen an explosion of cheap flash devices into the computer world. This has come so far that in 2009 we can only sit and laugh at very unreliable 1MB floppies and even 100MB Zip disks that you might see at computer junk stores. Already in Tanzania 2GB flash drives are common and, at least abroad, quality 16GB flash drives are inexpensive (35000/= TSH).

Camera memory (like SD cards) and USB flash drives rely on much the same technology so I will discuss them together.
The moving parts of the mechanical hard drive cause ~90% (?) of their failures. The Flash drive has no moving parts inside. This might make you think that this means the USB Flash has no chance to break. You would be wrong though. If you are working in a windows environment with lots of viruses you’ve probably seen flash drives break more than once.
My understanding of Flash drive technology is not perfect (see Wikipedia & other references below) but it seems that there are several ways to design flash drives that make trade-offs for speed, capacity, or longevity (longer life). Ideally you want a good amount of all three. I suspect that many cheap manufacturers may use fewer, cheaper chips inside their drives to make capacity very large while hiding the shortened lifetime and speed. (A technical discussion of these are made in a part of this article on flash-based hard drives)
Longevity, or the length of the life of the flash drive is talking about the amount of times you can Write and Read anything from your drive. For quality flash drives, these numbers are generally very large: Millions or billions of times. There are even very advanced algorithms in the drives which balance out the load to reduce the damage. But on cheap flash drives or under the assault of many very kali Windows viruses for weeks after weeks you can quickly find that your flash is at the end of its days.
Viruses want to spread. The instructions that code a virus are not written carefully to help your computer, the programmer is very lazy. In East Africa most viruses specifically want to spread through your flash drive. This makes it very important for a virus to make sure that it gets onto a flash drive at any cost. The virus writer does not care whether he kills your flash in a month. He just wants to get his bad instructions onto your flash. This means that he will often just have his program write Over and Over and Over again to your flash drive blinking its light all day long. When you’re doing a hundred reads and writes a minute, soon your millions and billions of operations are exhausted and gone.
If you notice your flash drive acting strange or slow you might only have a few more chances to rescue your data. Though you should always keep backups of your flash somewhere, in this situation make a special backup as soon as possible! You usually have a few more Read operations than Write operations with your drive and that could save your data. In the fourth tip of this series I will go into detail on the programs testdisk and photorec and which can be used to rescue files on a drive that Windows/Linux/Solaris will not read.
There are also major issues with fake drives. Beware! My counterparts here at Mpwapwa have seen several weak flash drives labeled “Sony Vaio” which will report to Windows (or Linux, Solaris) that they are, say, 32gb. When you put files onto them the files appear to transfer. This is fake though, the real size of the drive is 512MB. When you take files that are bigger than 512mb off of the flash again it will say that your file is corrupt. We have also seen that these flash drives fail much quicker than other flash drives.
Life and Death of Storage Devices 1: CD-R/DVD-R Discs
In Tanzania we are using 3 different kinds of hardware to store and share our data: CD-Rs/DVD-Rs discs, Flash drives, and (mechanical) hard disks. TZ is a harsh environment for each of these kinds of storage. I am sure you have seen each of them fail. The interesting thing is that each of them stop working in a different way. In this post I will describe the failure mode of each kind of device, as I understand them.

Dye on old CD-R is starting to dissolve, Via Wikipedia
CD-R/DVD-R:
CD-R and DVD-R are based on a similar idea. There is a layer of the disc which is reflective like a mirror. There is at least one other layer which has some special ink frozen in plastic and one more extra layer of plastic to try to protect the ink. The red laser inside the DVD or CD reader tries to change the ink or dye in millions of places/dots so that it can store data.
The most common way CD/DVD fail is by becoming scratched. As those of us that piga deki every couple days know, Africa is quite a dusty place–that dust scrapes at the plastic very easily leaving places where the laser is trying to read. Another possible way to damage a dvd is by breaking it so the ink spills a little or the reflective layer doesn’t reflect the laser back to the DVD player eye.
Perhaps the most interesting failure of CD/DVD is when a certain bacteria eats away at the reflective layer. Also if you buy certain DVD-R/CD-R the ink formula may be low quality and might not hold the dots “color” very well. As the “color” changes around the disc the data is slowly lost. If you leave a CD-R in the sun you might also notice data loss. There are more details on the Wikipedia page for CD-R.
For a larger hardware problem, with the dirt in the air, the mechanics of the CD-ROM drive often seem to fail so that the door to the drive does not open reliably. I have read some accounts that it is because the rubber band/string is getting stretched and so the drive doesn’t recognise that the eject button is pressed as easily. According to websites, you can replace the band and it will often start to eject properly again but we haven’t tried it at our college.
Umeme Uchafu and You.
Dirty electricity is a big problem in Tanzania. Viruses may cause most of Tanzania’s software problems but dirty electricity is accountable for most of the hardware issues that we find here. Unlike software, there is often no way to recover from a hardware failure without spending more money. That means even though in my mind a virus scanner is lazima–an unquestionable must, correct power protection is even more important.
The problem with power protection is that there is no wisdom on the issue from Western developed countries (unlike with viruses). There are power protection items available here in Tanzania that we can use to protect against the bad power here but they are often not widely understood. In the US and Europe there are not so many worries about power, besides perhaps lightening strikes.
I think the most important rule is to keep at least one piece of equipment between you and Tanesco. I recommend some of the devices below. Here are some options I researched last weekend at a certain direct dealer in downtown Morogoro (between dala stand & soko):
Prices are listed in TSH
- Voltage Regulation: Blue Samlex (not fake) Voltage Regulators, clean wild voltage to lengthen the life of laptop hard drives. Will not protect transformer explosions, etc.
- 500W (4 laptops or 1 desktop): 38500
- 1000W (2 desktops): 48500
- 1500W (3-4 desktops):62500
- Voltage surge protectors strips (protect from lightening or perhaps transformer explosion)
- Solatek Multiguard Surge+Spike (5 plug, 13A): 39500
- Tripplite: 24000 (?)
- Solatek AVS – Automatically cut the power if power is poor, return it after short timer. Free warranty service is available at AAPower on Zanake street in Dar es Salaam. I plan to visit this week.
- COMMGuard (1 desktop, laptop): 28500
- AVS 13A (3-4 desktops?): 70000
- AVS 15A (round holes, 5 desktops?): 78500
- AVS 30A (7-10 desktops?): 92500
I have not yet had a chance to price UPSs. Still, I would like to post the reminder that Laser printers & copiers should be protected separately from other devices as they suddenly draw huge amounts of currents when the toner lases (see wikipedia). If one is plugged into a UPS with a computer in the wrong port you will, in a short time, kill the UPS, computer and printer.
Kurudi tena
So the past 19 days since the only post this month have been very busy so I’ve been neglecting the blog. I hope to come back significantly this coming week. I have a new series on how different kinds of storage media devices fail in East Africa and a few prices on power coming up. The virus series is on my plate too.
Two weeks ago we installed the latest Solaris “image” at our college and installed several software updates after it. I’ve recorded my instructions and have shared it with the project so that the next version of the Solaris image can include only the freshest software like Adobe Acrobat reader, Firefox, and Open Office. In computer administration, an “image” is a very complete collection of all the configuration that is done to a computer. It is then arranged into a DVD or file so that it can be shared easily with other people (or colleges). When you install it, everything is already set up for you, just as the team at Morogoro left it. Later, I hope to cover imaging for Windows computers with Clonezilla to make your life easier.

Last week Peace Corps TZ officially added Windows virus and power protection to the skills that new volunteers are required to study and learn during their three month training, after Swahili. I think this underlines the situation here. I feel that viruses are getting more frustrating, even fewer of them are being detected by antivirus and there are many more of them. It also focuses us on power protection: please listen to my message in my umeme uchafu articles: spending a small amount now on prevention will save your departments a lot of money later.
I also held a small seminar here with a special guest from Mzumbe Mbeya to explain the benefits of Ubuntu Linux–it is always virus free (from flash drives) and has nearly all of the programs & features of Windows that Solaris is missing. Keep in mind that leaving Windows is an easier option than it sounds like when you get frustrated cleaning peoples’ USB flashes and slow computers. Just download, burn and install the CD. It installs much faster and easier than Windows. You can even order a free one to be sent to Tanzania! (linkage)
Virusi si jambo gumu: How Viruses Trick You Part 1 of 3
A flash drive in Tanzania may seem complicated with all of the viruses that can get onto them and cause every kind of problem. The problems with them that Tz computer users see every day all have pretty basic explanations, especially when they are still on the flash drive. In the next three virus tips I will explain:
-
the idea of a virus (this tip),
-
the way that most common USB Flash virus spread on to Windows XP
-
and their common hiding places.

Virus: Work is Work; Don't hate my work, it doesn't help me. Us: Take your panga somewhere else
In one sense, computer viruses are like biological viruses. Viruses have two goals:
-
To spread their instructions to other computer, and
-
To do something else
Any one virus does not want to completely break your computer with these goals. If it breaks your computer then it can’t spread from your computer to new computers and it is a weak virus. The “do sometime else” includes making our computers run slowly, do strange things, and sometimes stop working altogether. Usually after many viruses have arrived, they start interfering with each-other to make your computer very slow or crash.
Though viruses seem almost as dangerous and flexible as their biological viruses, they are written by people to spread a message, steal information, use your computer’s speed, or generally hurt Microsoft. As far as we know, no one writes viruses to deprive African school children of the opportunity to use computers but in our world, this is most often the effect.
We need to think about how viruses spread to help protect our computers from the first virus.
-
In Tanzania, the common way to spread a virus is through a USB flash drive when the user runs a virus program on it by double clicking on the main drive or fake items.
-
A few years ago in the rest of the world, email was the most common way to spread viruses. Here in TZ though, if you have a Yahoo email account, it already scans all your messages.
-
An important and often forgotten way viruses can come is when you download new software ovyoovyo without knowing that the person or website it is coming from is trustworthy. You should be very careful when you install internet software when it isn’t from a big company like Microsoft or Yahoo. The bad software is a like fake Chinese TVs or pasi–it looks almost right on the outside but inside it doesn’t work and might start a fire.
A virus usually cannot enter the computer through music or video. It needs to be free to give specific bad instructions to the central processing unit (CPU). Running programs talk to the CPU directly but playing music & video does not. This means that viruses can pretend to be music but that real music rarely has a virus inside. Also, clicking on a real folder cannot start a virus but clicking on a program with a picture (icon) that looks like a folder can be very bad. Viruses are computer tricks-Vinakudanganya kuwezesha kazi yake. The worst trick is one most Tz users don’t even see. They click fake movies and fake folders and dirty drives without seeing the virus.
Hata usipokuwa na virus scanner, If your Windows XP computer is updated to Service Pack 2 or 3 and you are careful , then there is no reason you should get any viruses. Your computer is not giving you viruses, you are being tricked to double click and run the virus program. If people on your computer never double click or right click your USB flash drive in My Computer, then you will never get viruses. Instead, you should find, click on the Folders button at the top and then left click once on your flash drive on the left side of the window as pictured.
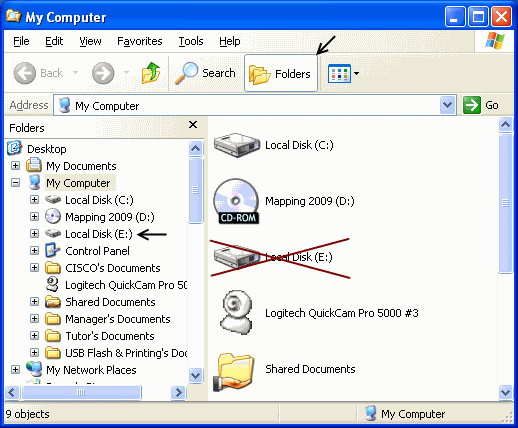
Screen shot showing the dangerous place to double click in My Computer. If you have an completely updated virus scanner you can worry less about this, otherwise be careful.
Why? Read the next tip on Autorun & Autoplay in Windows XP in this series on Viruses coming soon!
Some portions of this posting were written in collaboration with Aron, an A-Level teacher at Bihawana Secondary School.
Using WinSCP every day, for everyone
So now that umeishazoea kidogo kutumia WinSCP kila siku, there are some good tips for using WinSCP faster that are not obvious. Saved sessions make connecting only use a easy double click for either of your servers. The “Shell Icon” button can make it very easy to transfer documents to one place, like resources if you set the target Directory. I will explain these two things more below.
There are also some limits and warnings for using WinSCP.
- Sometimes the Root user is disabled for the SCP protocol for security reasons. You will not know if it is ready on your system until you test it.
- You will only be able to access or change the same files and folders that the username you logged in with is allowed to.
- Even students can use their accounts to log in to WinSCP but they will be fairly restricted to their normal place.
- There are a lot of grey Solaris hidden folders that show up in your Solaris Home directory when you look at it with WinSCP. You usually should not delete them as they hold settings for many of your user’s Solaris programs but you can hide them (or show them again) by pressing Ctrl-Alt-H all together.
Quick Sessions
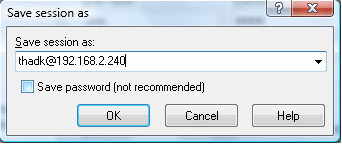
First, type your login information as you did last time–put either 192.168.2.240 or 192.168.2.242 in Host name (The IP addresses for Server 1 and Server 2, respectably). If you want to include your particular user as part of this shortcut, type that too. This time, instead of Login, press “Save…” button. Choose a name for your session, it will suggest something like thadk@192.168.2.240 and, if you typed it, use the tick to decide if you want to save the password for other people to access your account with this shortcut (see picture above). You will see that after you have saved one session, you will always start WinSCP on the “Stored sessions” item on the left side instead of “Session”! Now you can double click the session you saved to open it instantly or click on the Session item on the left to create a new one. If you typed a username before you saved, that is part of the session and you will not be able to type it again.
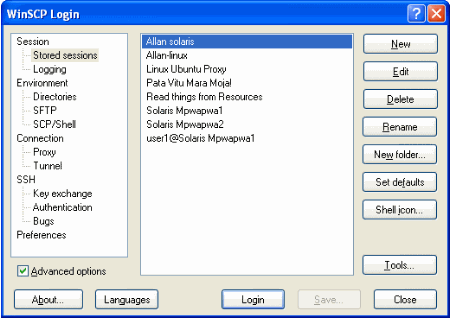
Making an icon that sends files to a Resources folder
Now do you see the Shell Icon button on the left in the picture above? We will use it soon. First, choose a session for the server with the resources folder on it by clicking it once, then press Edit. That will take you back to Session but you should go over to Directories. In Directories set the Remote Directory to your resources folder. At Mpwapwa TTC this is “/resources” without quotes. Now go back to Session and save your session again, maybe as “Resources”. Finally make sure your new session is highlighted, press Shell icon and choose either “Desktop icon” or “Send To…”.
Desktop icon will let you double click or drag files onto the icon to copy them into your resources folder. “Send To…” will let you right click any file and look down at “Send To->Resources” from anywhere in Windows. If you’ve saved your password and/or username you won’t have to enter them.
Remember that your permissions will be just as the user logged into Solaris themselves. If they are usually not allowed to write to the resources then they won’t be able to do it in WinSCP. Also be careful saving passwords. It is convenient but poor students or staff could steal your information using your session!
Thanks for reading, the next Solaris tip will be where to find videos and good resources to learn more about Solaris from Sun. The next Windows topic will be how to make hidden files show on your flash drives, followed by notes on keyboard short cuts to make using Windows (even Ubuntu or Solaris) more effective.
Controlling Computer Viruses in Windows
Viruses are a huge problem in Tanzania and most of Africa. Computers in Africa have many more viruses compared to the rest of the world. Parts of the problem may be that here virusi software siyo halisi and isn’t updated reliably because of the slow internet here.
In my experience, most Virus scanner companies are late to recognise viruses that come from East African countries so even if you have updates you are not always protected. Remember, the people that treat computer viruses and add them to the database are generally working in St. Petersburg, New York, or Israel; not Nairobi, Dar or Capetown.
Still, the first best way to deal with viruses is to keep your software up to date. No matter which software you use, it must be updated as often as you are bringing new viruses to the computer. This can be every week or every month. It depends on your computer. There are many virus scanners at FileHippo–some are Trial Versions but in order to get updates, you usually have to go into the software.
If you know where to find them, you can download offline files for the updates to use from your USB Flash Drives. Some versions of McAfee have programs to update with a file that you can download here (sdat). Some other company’s update files (Norton, Avast) can be found listed near the bottom of this page.
When I get stuck with those tool in Normal mode, the best way I have found to deal with viruses in Tanzania is to use Safe Mode (F8 while starting Windows), my normal Virus Scanner and the Sysinternals Suite from Microsoft. The main two programs I use from the Suite are autoruns.exe and procexp.exe. The package of tools is updated about once every two months to see more secret virus hiding places in Windows. Remember: your normal virus scanner will always work best from Safe Mode. If it does not work in normal mode (“failed to remove”), then you should try in Safe Mode.
Here are some rough instructions:
- Turn on computer.
- right away, press F8 repeatedly in the first screen to get the option of Safe Mode
- Choose Safe Mode with Networking
- Safe Mode is a special mode where the programs that normally come when you start the computer do not come.
- If Safe mode gives a blue screen or restarts immediately then you have a very kali virus and you need to try to clean it from normal mode. You probably won’t be able to fix Safe Mode without reinstalling Windows.
- Press Yes to enter safe mode when it asks.
- Update your virus scanner from file that you downloaded if you could not update before. You can probably not install a new virus scanner in safe mode.
- Start the virus scanner from the start menu (On-Demand scan for C: drive)
- Start a scan.
- If you cannot find anything, Copy Autoruns.exe to the computer, newer version will work best to find new viruses hiding places (optional)
- On the virus scanner, when it has finished make sure all the viruses confirm “Deleted” status as action taken.
- If that has not worked, Unzip and open Autoruns.exe, wait for it to load.
- After it loads enable both Options->Verify Code Signatures and Options->Hide Microsoft & Windows Entries.
- Press refresh.
- Look through the list of items that will start. You can temporarily disable things that look suspicious with the checkbox or right click and delete permanently. Be a little bit careful about mouse and keyboard items.
- Reboot.
Next topic in viruses: How to make all hidden files from Viruses on Flash Drives appear.


42 comments